Carve-out transactions involving data: two essential considerations you need to make

Carve-out transactions (i.e. the sale or purchase of a subsidiary, a division or other part of a larger business enterprise/group) will often raise a number of important issues for both the seller and the buyer when it comes to the split and transfer of the business data involved. Understanding these issues, and taking the right actions, is becoming increasingly important in M&A transactions and traditional approaches to M&A will often not provide sufficient protection.
In carve-out transactions, data is often shared, bundled or otherwise located “outside” the carved-out business.
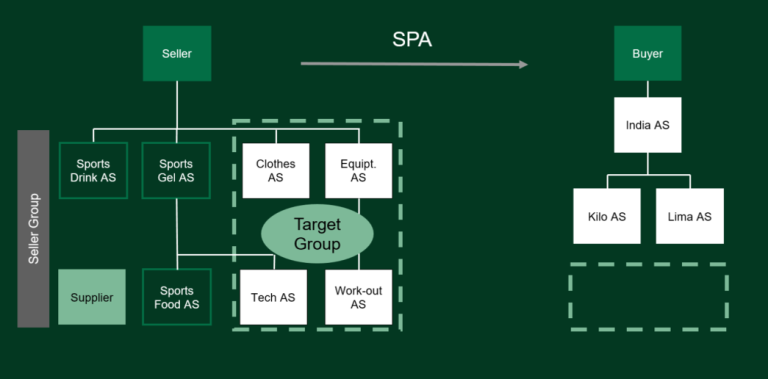
Illustration 1: Example of transaction structure
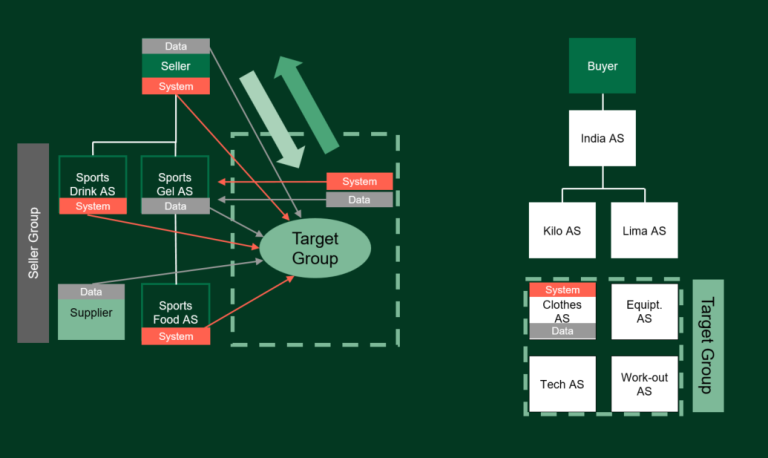
Illustration 2: Detailed transaction perimeter where the data pertaining to the Target Group is in fact located in the Seller Group, and vice versa
This results in some key concerns:
- How will you get comfort that the data needed to operate the carved-out business is actually transferred or made available to the buyer; and
- How can and will the carved-out business utilise the relevant data post-closing?
If these concerns are not properly addressed, the seller may not get paid full value for the business, the buyer may not get what it is looking for and, in the worst case, the transaction may end up collapsing as a result.
With this back-drop, this newsletter raises two considerations which it is essential to take into account prior to entering into a carve-out transaction.
Consideration 1: Conduct a mapping to get an understanding of who possesses and controls the data
Data as an “asset” has no legal framework and there is no specific law that regulates the ownership to data “as such”, unlike what is normally the case for the traditional IP-rights, such as patents, copyrights, trademarks and trade secrets. In general, without any restrictions in law or agreement, the “owner” of the data will in practice often be the party that actually “possesses” and “controls” the data.
To provide and get comfort in carve-out transactions, it is essential that both the seller and the buyer conduct a mapping of the business in question to understand (i) where the data is located, (ii) what it is used for, (iii) whether there are any restrictions on use and (iv) if and how the data should be transferred in the transaction. Since possession and control of data is key, it is important to make sure;
- if you are the seller,
- that no data you want to retain is in fact located in the carved-out business, and
- that commercial sensitive data which you do not want the carved-out business to have access to post-closing is sufficiently “ring fenced” (i.e. that prior access is restricted, the data separated or that access control is implemented);
- if you are the buyer,
- that no data you need for the acquired business is located in the business retained by the seller; and
- that commercial sensitive data which you do not want the seller to have access post-closing to is sufficient ring-fenced; and
- in any case, that data which is supposed to be part of the transaction can actually be transferred in practice (i.e. no restrictions, either by law or contract).
Further, a clear understanding of the above key elements is important for the parties’ legal protection. Simply stating in the purchase agreement that “all data pertaining to the carved-out business shall be transferred” (or similar types of wording) will in many cases not be sufficient legal protection, since;
- the data is also often used by the seller’s group, which means that this type of wording will not give a clear answer as to who has the right to the data;
- certain data can be bundled and may in practice not be possible to transfer separately; and
- the wording will likely not capture the actual structuring of data or any embedded data, just the underlying raw data.
To summarise, a mapping is essential to identify who possesses and controls the data. Being in possession and control of the data will give you better protection, both legally and in practice. If you do not possess the data, you need to be (more) diligent in the mapping and be specific on what you need in the transaction agreements.
Consideration 2: Data vs. user accounts – what do you really need?
In general, it is important to understand how the data is utilised and how to best utilise the data going forward when transferring and integrating the data to a new (receiving) environment and structure. A specific topic in this context is how to consider user accounts with pertaining data in carve-out transactions.
More and more often, data is integrated with the IT-system in which it is used, in particular when it comes to algorithms and AI that utilise and create knowledge regarding the use of data. Therefore, in many cases, it is not possible to separate the data from the system in which it is embedded.
For example:
In the above illustrated carve-out transaction of the target group, half of the target group’s revenue is created by ad-tech and generated through online advertisement on Facebook or other channels. Such online advertisement is based on quality data regarding consumer groups securing specific and targeted marketing, developed over time, and all such data is located in seller’s google analytics account. If you as the buyer agree in the transaction agreement to only get “the data pertaining to the target group business” and not the actual user account, you will have to start at scratch post-closing on building new quality data and you will lose the knowledge embedded in the user account developed over time. As an effect, the advertisement will likely be poor and not sufficiently targeted for a period post-closing, which in turn may result in lost revenue.
In other words, the real value lies in the user account, and not in the data itself. When engaging in a carve-out transaction, a key consideration should therefore be whether the data itself is enough, or if you need the actual user account with the knowledge and embedded structured data.
Wiersholm’s M&A Tech group has broad experience in advising on the issues related to transfers of data in M&A transaction. Please reach out to our team if you want to discuss.
Kontaktpersoner
Publisert:
Sist oppdatert: